HTTP alternative services and opportunistic encryption
HTTP Alternative services allow an origin’s resources to be authoritatively available at a separate network location, possibly accessed with a different protocol configuration.
Opportunistic Encryption (OE) provides unauthenticated encryption over TLS for data that would otherwise be carried via clear text. It allows a http:// connection to use secure resources.
Update : Mozilla has disabled “opportunistic encryption” to fix HTTPS-crippling bug in Firefox 37.0.1 :(
You can read a good introduction on Mnot blog. I think this quote is a good summary :
It doesn't help at all with active attacks; for example, it's trivial to downgrade this mechanism to plaintext by simply removing a header. Furthermore, Firefox currently doesn't check the certificate when using TLS for http:// URLs, so an attacker can pretend to be the server and the browser won't be the wiser.
In other words, if you want real security, you still need to use "full" https://.
Today I read on Patrick McManus blog that Opportunistic Encryption will be available in Firefox 37 ! (the bug report).
I have a self signed certificate, so let’s go for some testing !
I use nginx, thus I only need to modify my configuration to add the Alt-Svc header in my blog’s virtualhost.
add_header Alt-Svc 'h2=":443"; ma=60';
# It seems that it works too with "spdy/3.1=:443".
You can specify another host, for example h2=”secure.alteroot.org:443”. In this case, secure.alteroot.org must present a valid certificate for blog.alteroot.org (see the rfc, Clients MUST NOT use alternative services with a host that is different than the origin’s without strong server authentication.)
The “ma” is ‘max-age’, which indicates the number of seconds since the response was generated the alternative service is considered fresh for (default 24h). According to my tests, once the max-age is expired ( 60 sec without requests in this example), the browser reuses plain http request.
Of course your service must be configured on port 443 with an ssl certificate (even selfsigned).
Here a screenshot of Firefox 37 inspector.
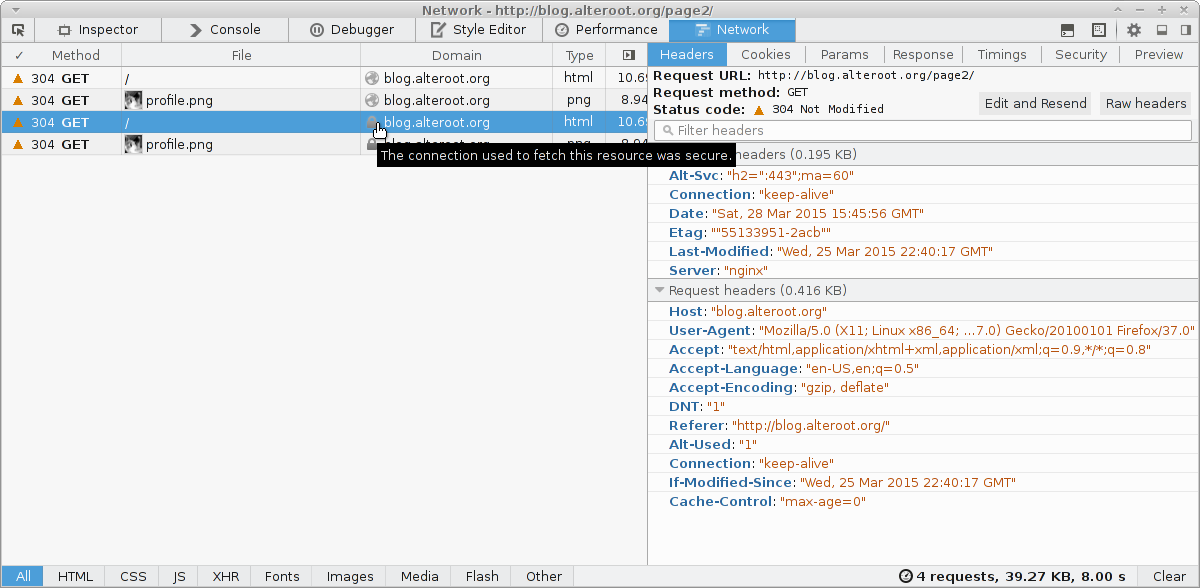
You can see that I request http://blog.alteroot.org (first two requests), then I refresh : now my request use encryption !
You see the Alt-Svc header sent by nginx, and the client header “Alt-Used: 1” (When a client uses an alternate service, it MUST emit the Alt-Used header field on every request using that alternate service.).
And no certificate warning !
In my nginx log, I can see that the browser use a secure channel :
[28/Mar/2015:17:23:09 +0100] "GET /page2/ HTTP/1.1" 304 200 "http://blog.alteroot.org/" "Mozilla/5.0 (X11; Linux x86_64; rv:37.0) Gecko/20100101 Firefox/37.0" blog.alteroot.org:443 ECDHE-RSA-AES128-GCM-SHA256 TLSv1.2
At the moment, only Firefox 37 support alt-svc for Opportunistic Encryption. A chromium implementation is under development.